Reached over 5 million active installations and gained thousands of 5-star reviews from users in every corner of the world, Contact Form 7 proves one of the most favored contact form plugins out there.
Offering useful features free of cost meeting the needs of both bloggers and businesses, it doesn’t blow your socks off that the plugin receives over 112 million downloads up to now.
However, the immense popularity often comes with a cost. Over the years, users have discovered many security flaws in this plugin that make Contact Form 7 an ideal bait for attackers.
Among them, an unrestricted file upload vulnerability resulted in millions of WordPress sites getting hacked.
In this article, we will give you a clear explanation of this Contact Form 7 vulnerability as well as highlighting effective tips to fix it.
Get to Know Contact Form 7 Vulnerability
A vulnerability was discovered in Contact Form 7 in December last year by the Astra research team. It was related to an unrestricted file upload issue found in all 5.3.1 versions and lower.
According to the WordPress plugin directory, over 5 million sites were using Contact Form 7 at the time. However, the actual number could reach 10 million, as to WordFence estimation.
Compared to other contact form plugins that require users to install add-ons to enable the file upload feature, Contact Form 7 itself gives the green light to that feature as a part of form submission. This accidentally did pose a security threat that forced the plugin to quickly release a security patch to fix it.
What is an Unrestricted File Upload Vulnerability?
The Contact Form 7 vulnerability permits an unauthenticated user to bypass the filename sanitization. Its main duty is to block certain restricted file names, allowing whitelisted file names only, and control the file paths.
In other words, the unrestricted file upload vulnerability causes your website to accept some blacklisted file formats, namely PHP or ASP. They execute commands and functions on your site.
Plus, it also paves the way for attackers to upload malicious scripts to the WordPress uploads folder; specifically /wp-content/uploads/wpcf7_uploads/. Once the file is uploaded, those scripts will harm your sites, which may result in security breaches, data theft, and other potential damages to files and computing systems.
In particular, they can:
- Navigate users to malicious, gambling, or adult websites.
- Change your site’s content to sell/promote drugs or illegal products.
- Form a backdoor that will let attackers break into your site at any time.
- Create ghost admins that will grant access to unwanted users via your login page.
The question is, will deleting the contents of the wpcf7_uploads folder resolve the problem?
If you think removing the malicious content in the wpcf7_uploads/ folder can bring things back to normal, this is completely a serious underestimate.
The Contact Form 7 vulnerability acts as a door to hackers to penetrate your site. Once the door is opened, they gain complete access and start to infect and tamper with dozens of files and databases.
How to Fix the Contact Form 7 Vulnerabilities?
Right after the vulnerability was found, the developer behind Contact Form 7 – Takayuki Miyoshi strived to fix the issue as quickly as possible, realizing the severity of the problem.
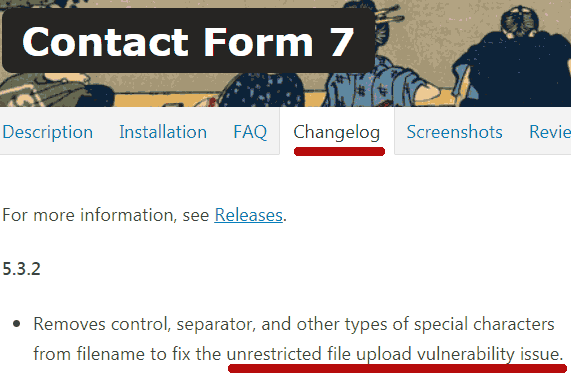
A security patch was released right off the bat, just a day later, with the update of Contact Form 7 5.3.2.
He called the update “an urgent security and maintenance release,” which:
“Removes control, separator, and other types of special characters from filename to fix the unrestricted file upload vulnerability issue.”
If you are using Contact Form 7 without the file upload function, your site is free from shielding off hackers attempting to exploit this vulnerability. However, we still recommend you take the immediate actions given below to enhance your site security properly.
#1 Update Contact Form 7 Immediately
The Contact Form 7 vulnerability in version 5.0.4 had been fixed. If you’re using Contact Form 7 on your site, we highly recommend you update it to the latest version, which is version 5.4.
Once the vulnerability is swept away with the update, hackers can no longer use the similar one to break into your site.
#2 Find and Remove the Malicious Scripts
As we mentioned before, deleting the infected folder will provide no help to fix the issue. To pinpoint and resolve malicious scripts, you must seek the assistance of malware scanners.
They allow you to not only scan for vulnerabilities but also block malicious networks and implement a firewall with a light touch. There are a variety of outstanding WordPress security plugins in this field, which several experienced veterans are MalCare and Wordfence.
MalCare
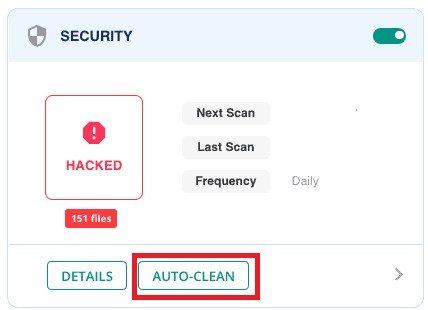
MalCare Security plugin enables you to detect malicious scripts by scanning your entire site. All of the hidden and unknown malware in your files and database will be tracked down and brought to life on the spot.
What’s more, the Auto-Clean feature ensures the process of rooting malware out takes place smoothly without deleting entire files or breaking a code.
Wordfence
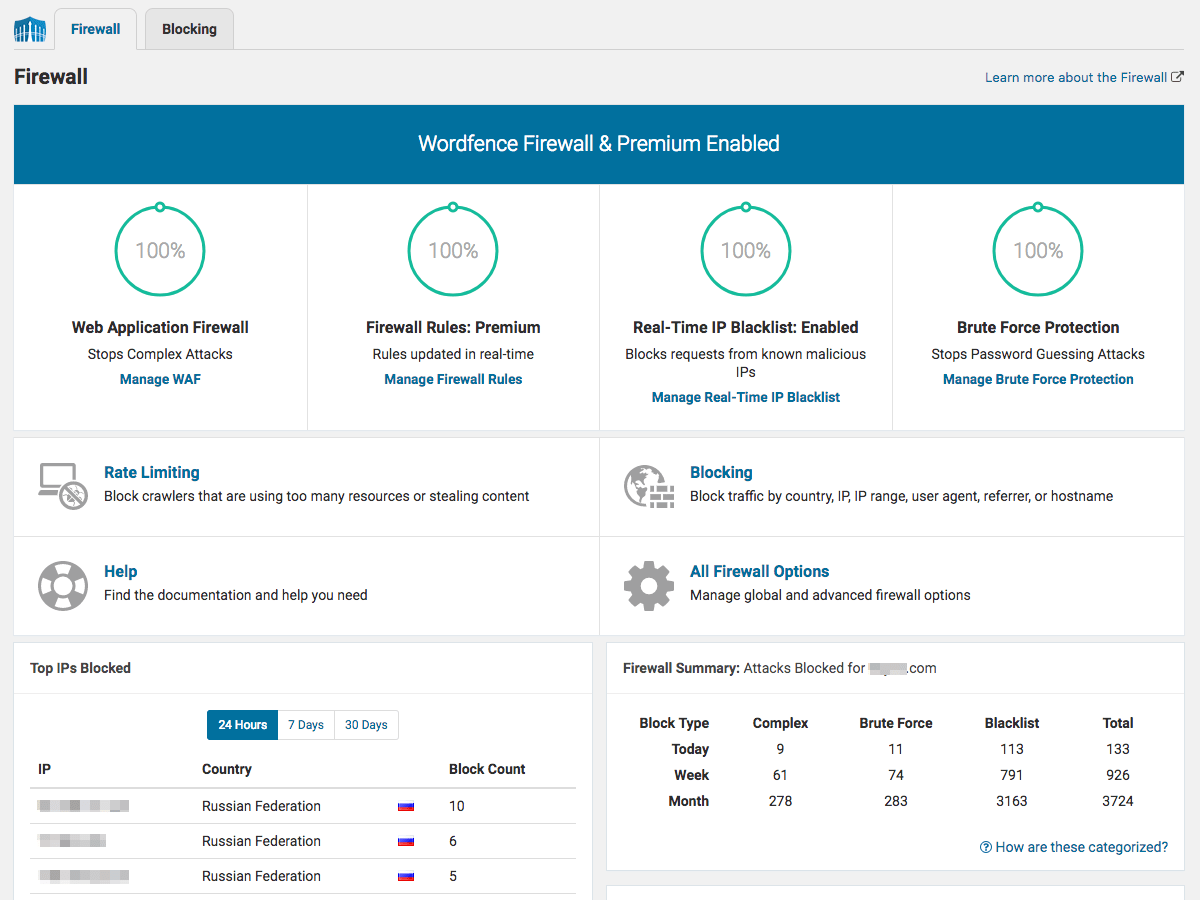
Wordfence makes the hack removal process just a walk in the park thanks to its endpoint firewall and malware scanner. In particular, it scans core files, themes, and plugins to detect malware, backdoor, malicious redirects, and code injections.
The plugin also checks and alerts you whenever it spots any known vulnerabilities or potential plugin security issues on your site. On top of that, you’re free from worrying about content safety, as it scans the content in every file, post, and comment for suspicious one and dangerous URLs.
#3 Remove Ghost Admins
Attackers can make use of the Contact Form 7 vulnerability to create fake administrators. A ghost admin normally stays unnoticed to most site owners since it is just a subtle change.
However, its damage to your site is incalculable. Even if you can remove malware from your WordPress site, no malware scanner will be able to detect a fake admin user.
To save your sites from ghost admins, you must configure WordPress user settings. We recommend you back up your site before making any changes.
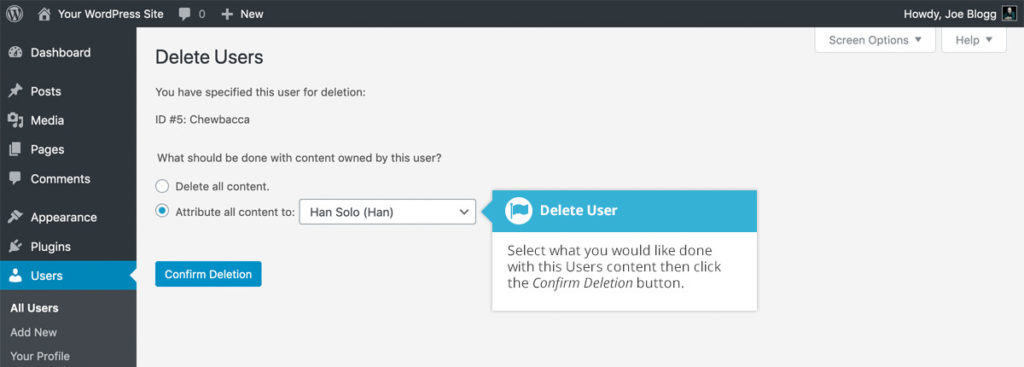
- In your WordPress dashboard, go to Users > All users.
- Hover over the username you want to delete. Click “Delete,” which takes you to a “Delete Users” page.
- Between the 2 provided options: Delete user posts and Attribute all content to, choose the latter.
- Select the new username as the new author for these posts.
- Click Confirm Deletion.
#4 Harden WordPress
Once you successfully patch the Contact Form 7 vulnerability by using the 3 steps above, it’s time to harden your WordPress site to stop security threats at a doorstep. Following are some recommended tips to safeguard your sites from future attacks.
Create Unique and Strong Passwords
To create strong passwords, first and foremost, you must avoid using common adjacent letters or numbers. An ideal password should be a combination of letters, numbers, and symbols. Don’t forget to reset your passwords regularly after every 90 days.
Install WordPress Security Plugins
Utilizing WordPress security plugins is the safest solution for protecting your site from any type of attack, including malware. You can consider 2 plugin options that we’ve recommended above.
Limit Login Attempts
By default, WordPress set a limitation on the number of login attempts. Limiting login attempts on your website helps tighten security and concurrently reduce the high chance of your site getting brute force attacks.
For the complete guide on restricting login attempts, please refer to this article.
Always Keep Everything Updated
Paying attention to keep your WordPress sites, plugins, and themes up to date is the top priority. New versions will include better-advanced features and fix the vulnerabilities of the old ones.
Apart from that, remember to use original plugins or themes from trusted websites. This is because they come with regular updates and security support channels for any spotted issues.
Stop Security Threats through Contact Form 7
This post has broken down the term of Contact Form 7 vulnerability in unrestricted file uploads, as well as putting forward actionable tips to fix that issue.
If you’re using Contact Form 7, bearing in mind to update it constantly. Plus, don’t forget to take installing security plugins, removing ghost admin accounts, and hardening your WordPress sites into serious consideration.
In case you don’t feel secure with Contact Form 7, there is a wide range of Contact Form 7 alternatives for you to choose from. The choice is yours!
If you have any questions related to WordPress Contact Form 7 vulnerability, feel free to post them in the comment section below! We’ll sort them out as soon as possible!